
Networking
With the purpose of creating a device capable of independently solving the most common problems, Antek developed ABILIS on five principles:
- Ensuring extremely resilient connectivity by using multiple Internet lines in parallel simultaneously.
- Allowing clients to choose the network providers and services they prefer. Antek simply suggests selecting lines that follow well-differentiated routes.
- Avoiding potential network congestion caused by self-induced traffic overloads. These events are far from uncommon, often corresponding to software updates or unreasonable downloads.
- Using multiple Internet lines and FEC (forward error correction) to reduce re-transmissions, as it happens in storage systems with RAID.
- Mitigating cyber-attacks through various measures:
– using fresh black-lists from institutions delegated to fight cybercrime.
– dodging denial-of-service attacks and blocking brute-force attempts to guess passwords.
– using an intrinsically secure VPN.
– filtering out spam and malicious e-mails.

Why choose Abilis?
Because of a better service continuity:
- The simultaneous use of multiple lines and the absence of an ‘operating system’ leave no foothold for hackers.
- A failure or attack on a single line only causes a reduction in connection speed.
Because your ‘public’ IP addresses will always remain unchanged, even when you change connections and use assorted lines and providers.
Because of a guaranteed backup: the constant use of all available lines ensures an immediate alert in case of any line failure.
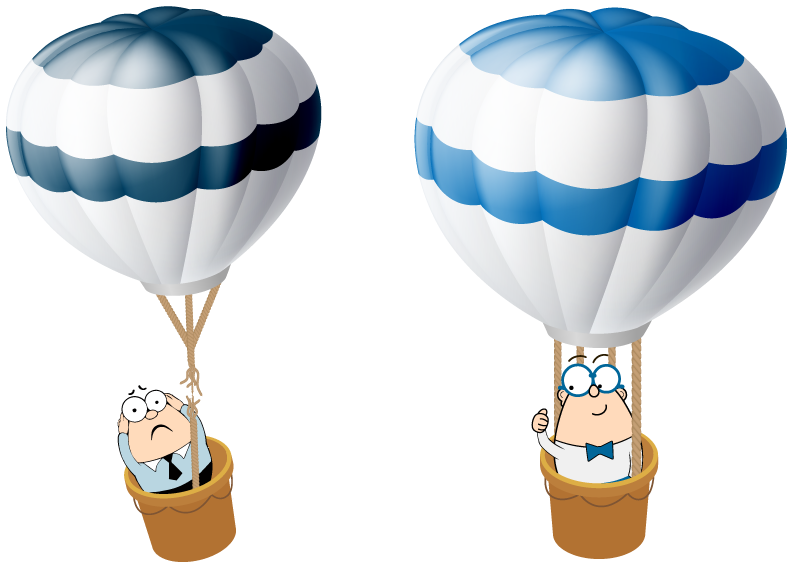
One line only: RISK ! Multiple lines: NO RISK !
Place a VPN router of your own next to the servers in your Cloud
The main user of cloud services is often the same company publishing them, hence the connection to the Cloud is vital.
By installing a virtual ABILIS router in the same environment (AWS, AZURE, …) where their cloud-servers are deployed, publishers establish a strong multi-line connection from their headquarters to their servers.
Monitoring and Control
Our concept is that the router itself must prevent and resolve overuse events, thus saving the resulting warnings.
The ABILIS embedded automatic congestion avoidance controller (IPSH) is able to recognise excessive traffic between ‘machines’ and to postpone it with respect to interactive sessions (man to machine).
IT systems, used to update programmes or synchronise DBs quite anarchically, will no longer slow down users’ sessions.
System administrators can read the main origins and destinations of data-traffic sent/received by each LAN host without necessitating any dedicated Network Management tool.
They can also build up a Blacklist of unwanted correspondents and a Whitelist of privileged ones. But the Blacklist can also be fed automatically, on the base of predefined rules.
Multi-Level Security
Because of the rock solid VPN, based on the ABILIS router itself.
Because of the detection and solution of issues caused by own computers, prioritizing interactive sessions over bulk data transfers.
Because of the embedded traffic control system, comprehensive, understandable to everyone, and objective.

