| 49.6. Aggressive Mode: Example of IPSEC configuration | ||
|---|---|---|
 | Chapter 49. IPSEC - Internet Protocol SECurity | 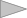 |
Consider an IPSEC VPN in TUNNEL mode that uses the IKE protocol and an ANONYMOUS access, as shown in the following figure.
![[Caution]](../images/caution.png) | Caution |
|---|---|
The IPSEC connection works ONLY if the LAN, where the PC client is connected to, is different from the LAN of Abilis (e.g. in the previous case if the PC client IP address is belonging to the 192.168.1.0/24 the IPSEC connection doesn't work!). |
![[Tip]](../images/tip.png) | Tip |
|---|---|
Interesting chapters: Section 81.19.1, “How to configure a RAS using IPSEC VPN server”; |
Set the IPSEC parameter to
YES in the IP resource in which you want to
encapsulate IPSEC packets (outgoing traffic). If you want to use the
IP-2 resource (ADSL line), type:
[15:54:12] ABILIS_CPX:s p ip-2 ipsec:yesCOMMAND EXECUTED [16:08:53] ABILIS_CPX:d p ip-2RES:Ip-2 - IP over PPP (PPP) -------------------------------------------------- Run DESCR:ADSL_line OPSTATE:UP LOG:NO STATE-DETECT:NORMAL LOWRES:Dsl-1 IPADD:RETRIEVE NEIGH:RETRIEVE REDIS:EXT HIDE:NO RP:NONE IPSEC:YES VRRP:NO NAT:OUTSIDE UPNP:NO DIFFSERV:NO DDNS:NO OUTBUF:100 OUTQUEUE:FAIR MTU:1500 OUTSPL:NO INBUF:0 mru:1500 SRCV:NO - TRFA section --------------------------------------------------------- TRFA:NO - Ppp ------------------------------------------------------------------ LOG:DS NRTY3:3 PPP-ENC:RFC2364-VCMUX RADIUS:NO VPI:8 VCI:35 - Tcp-MSS/Lcp/IpCp ----------------------------------------------------- TCP-MSS-CLAMP:NO maxmru:1500 DNS:NO - Authentication ------------------------------------------------------- USERNAME:abilis PASSWORD:******** LOCAL:CHAP,PAP SERVNAME: REMOTE:NONE REPEAT:0 RES:Dsl-1 - Not Saved (SAVE CONF), Not Refreshed (INIT) ----------------------- ------------------------------------------------------------------------ DESCR: LOG:DST MODE:ADSL payload-rxbuf:30 - Specific for Abilis-VDSL2 modem -------------------------------------- MORE-ADSL-ANNEX:L,M - Specific for Abilis-5800UB modem ------------------------------------- 5800UB-MODULATION:AUTO - Adsl-ATM ------------------------------------------------------------- max-vc:1 adsl-usb-rxbuf:3 adsl-usb-txbuf:1 - Vdsl-PTM ------------------------------------------------------------- vdsl-usb-rxbuf:15 vdsl-usb-txbuf:15
![[Caution]](../images/caution.png) | Caution |
|---|---|
To activate the changes made, execute the initialization command init res:ip-2. |
Add an IKE Host with Aggressive mode:
[16:06:36] ABILIS_CPX:a ike host:0 name:User_1_Aggressive mode:aggressive
COMMAND EXECUTEDGive the host the following characteristics:
local IP used for the VPN: 81.81.81.81;
ip resource used for the VPN: IP-2 (ADSL line);
no verify of the client's IP address that tries to open the VPN;
authentication method: PSK;
hash algorithm: SHA1;
Diffie-Hellman group: MODP1024;
encryption algorithm: AES256;
NAT type: INSIDE;
XAUTH authentication;
Peer ID type: KEY-ID.
[16:16:33] ABILIS_CPX:s ike host:0 locip:81.81.81.81 remip:*COMMAND EXECUTED [16:16:59] ABILIS_CPX:s ike host:0 auth:PSK hash:SHA1 dh:MODP1024 cipher:AES256COMMAND EXECUTED [16:17:09] ABILIS_CPX:s ike host:0 side:insidexauth:server xauth-user:user1 xauth-pwd:user1pwd COMMAND EXECUTED [16:17:21] ABILIS_CPX:s ike host:0 mode-cfg:request peer-id-type:key-id peer-id:mykey202COMMAND EXECUTED [17:55:47] ABILIS_CPX:d ike host:0- Not Saved (SAVE CONF), Not Refreshed (INIT) --------------------------------- ------------------------------------------------------------------------------- HOST: NAME: LIFETIME: HASH: DPD: DPD-ACTION: LOCIP: NATT: MODE: MODE-CFG: DH: DPD-DELAY: REMIP: SIDE: AUTH: XAUTH: CIPHER: SA-TRY: DPD-TOUT: XAUTH-USER: XAUTH-PWD: -- PSK ID --------------------------------------------------------------- ID-TYPE: IP:/ID: PEER-ID-TYPE: PEER-IP:/PEER-ID: -- RSA Cert ------------------------------------------------------------- CERT-SEND: ASN1-DN: CERT-PEER: PEER-ASN1-DN: CERT-VERIFY: ------------------------------------------------------------------------------- 0 User_1_Aggressive 3600 SHA1 YES STOP 081.081.081.081 SYS AGGRESSIVE REQUEST MODP1024 30 * INSIDE PSK SERVER AES256 3 120 user1 ******** -- PSK ID --------------------------------------------------------------- LOCIP KEY-ID mykey2020 -------------------------------------------------------------------------------
![[Caution]](../images/caution.png) | Caution |
|---|---|
To activate the changes made, execute the initialization command init res:ike. |
Add an IKE client:
[16:29:57] ABILIS_CPX:a ike cli:0 name:user_1_cli
COMMAND EXECUTEDGive the host the following characteristics:
IPSEC negotiation: tunnel mode;
IP address of the server: 192.168.1.0/24;
IP address of the client: 192.168.200.1/32.
[16:30:15] ABILIS_CPX:s ike cli:0 host-id:0 tunnel:yesCOMMAND EXECUTED [16:30:33] ABILIS_CPX:s ike cli:0 net-loc:192.168.1.0/24 net-rem:192.168.200.1/32COMMAND EXECUTED [16:40:16] ABILIS_CPX:d ike cli:0- Not Saved (SAVE CONF), Not Refreshed (INIT) --------------------------------- ------------------------------------------------------------------------------- CLI: NAME: LIFETIME: ESP: AH: HOST: NET-LOC: RULE: PASSIVE: PFS: ESP-AUTH: AH-AUTH: NET-REM: PERMANENT: TUNNEL: ESP-CIPHER: MODE-CFG-DNS: ------------------------------------------------------------------------------- 0 user_1 28800 YES NO 0 192.168.001.000/24 IPSEC YES YES SHA1 SHA1 192.168.200.001/32 YES YES AES256 SYS -------------------------------------------------------------------------------
![[Caution]](../images/caution.png) | Caution |
|---|---|
To activate the changes made, execute the initialization command init res:ike. |
If a PSK authentication is set in the IKE Host table, you must define a secret key for mutual authentication. In our example type for an KEY-ID PSK:
[16:51:32] ABILIS_CPX:a ike psk:0 key:preshared_key peer-id-type:key-id peer-id:mykey2020
COMMAND EXECUTED
[16:52:11] ABILIS_CPX:d ike psk
- Not Saved (SAVE CONF), Not Refreshed (INIT) ---------------------------------
-------------------------------------------------------------------------------
PSK: KEY: PEER-ID-TYPE: PEER-IP:/PEER-ID:
-------------------------------------------------------------------------------
0 ******** KEY-ID mykey2020 ![[Caution]](../images/caution.png) | Caution |
|---|---|
To activate the changes made, execute the initialization command init res:ike. |
Ensuring that outgoing IPSEC packets are routed toward appropriate resource is important.
Add a static route for remote network (in our situation only for host 192.168.200.1/32) towards IP-2 resource (specifying eventually the gateway).
[16:51:32] ABILIS_CPX:a ipr net:192.168.200.1/32 ip:2COMMAND EXECUTED [16:52:17] ABILIS_CPX:d iprDestination routes and conditional source routes: +-+-+-+-+--------------------+--------------------+-----------------+----+---+ |B|P|S|H| NET:/MASK: | MASK: or | GW: or |IP: |AD:| | | | | | | SRNET:/SRMASK: | IPLB | | | +-+-+-+-+--------------------+--------------------+-----------------+----+---+ |*|C| | | 081.081.081.081/32 | 255.255.255.255 | |R-ID| 0| |*|C| | | 192.168.000.000/24 | 255.255.255.000 | | 1| 0| |*|S| | | 192.168.200.001/32 | 255.255.255.255 | | 2| 1| |*|S| | | 000.000.000.000/0 | 000.000.000.000 | | 2| 1| +-+-+-+-+--------------------+--------------------+-----------------+----+---+